|
|
|
Cryptome DVDs are offered by
Cryptome. Donate $25 for two DVDs of the
Cryptome 12-years collection of 46,000 files from June 1996 to June 2008
(~6.7 GB). Click Paypal or mail check/MO made out to John Young, 251 West
89th Street, New York, NY 10024. The collection includes all files of
cryptome.org, jya.com, cartome.org, eyeball-series.org and iraq-kill-maim.org,
and 23,000 (updated)
pages of counter-intelligence dossiers declassified by the US Army Information
and Security Command, dating from 1945 to 1985.The DVDs will be sent anywhere
worldwide without extra cost. |
28 February 2006
James Atkinson (www.tscm.com):
I have a method of faking the remote control codes and/or passwords for the
Spectronics (DK) line of eavesdropping devices.
This allows a TSCM specialist the ability to "blink" a Spectronics bugging
device on for a second or two to detect it, and then to shut it back down
before the eavesdropper catches on to the fact that his bugging device has
just been caught. There is a small number of 12 bit "house" activation codes
that can be run though in less than a second, but they are only 6-8 in total.
If you can't hit it with the basic sequence then you will have to run though
the full 12 bit sequence which will till take you less than ten minutes.
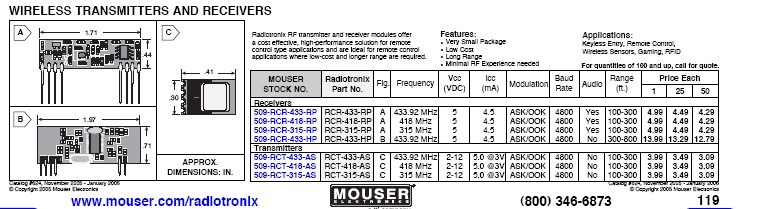
The signal is transmitted at 433.92 MHz as a AFSK data stream so most of
you will have no problem getting the bug to give itself up (cracks about
Prom dresses not withstanding).
The entire RF TRANSIT section shuts down when these things go into sleep
mode, but the RECEIVE section stays awake on monitors the command channel
all the time. The bugs are EXTREMELY easy to find them if you can use the
bypass codes (less than a second), or the full sequence (less then 10 minutes)
due to the small size of the activation key, and known activation frequency.
You can also find these little bugs by purchasing 8 ea car alarm remote (12+
bits) and simply pressing the button of each remote in sequence. You will
need to reprogram in each of the remote activation codes into the remote,
but your only talking about a sequence that is two bytes long (please stop
laughing at such a simple method to find them).
A company called Oregon Scientific and Davis Instruments makes a line of
Wireless Digital Thermometers that operate on the same frequency as, use
the same bit stream as, and operate similar to these Spectronics Eavesdropping
devices. The only problem with these thermometers is that if you have a
Spectronics eavesdropping system nearby you run the risk of accidently activating
the eavesdropping device during a bug sweep as the weather changes (cough-cough,
nudge-nudge, wink-wink). Hand held code grabbers used by the car alarm and
garage door opener industry also make short work out of tracking these devices,
but their possession and/or use may cause legal issues.
To run through the entire sequence of house command signals you only need
to spit out 128 bits of data, or 16 characters. This is important as you
can also use a wireless keyboard that operates at 433.92 MHz which uses the
same format and merely type in the 16 character "all on" sequence via the
keyboard, but using the car alarm remote is a little easier. If you end up
having to search for all 12 bit variations then you wouldn't want to use
the car alarm method and would need something that could tumble the entire
sequence.
Spectronics is not the only company to use either this frequency, nor are
they the only ones to use the 12 bit activation code. If you really want
to take an eavesdropper to the ground you can issue the same sequence at
310 MHz, and 916 MHz at the same time you were transmitting the 433 MHz codes.
Here is the command structure, so if somebody wants to really play with the
remote controls that will need to pulse out the following (it is a four bit
command word, in addition to the addresing word of 12 bits).
0 TX on
1 TX off (factory default)
4 TX audio scrambler on
5 TX audio scrambler off (factory default)
A TX OOF-HOOK defeated (factory default)
B TX with OFF-HOOK control, line voltage = 10V DC
C TX with OFF-HOOK control, line voltage = 20V DC
D TX with OFF-HOOK control, line voltage = 40V DC
E Start up state after DC removal: TXoff
F Start up state after DC removal: Same as before DC removal (factory default)
The "scrambling" used by the audio circuit eavesdropping system is simple
frequency inversion that many scanners can monitor, or which anybody can
decode and listen to on a PC. Anybody who is in the middle of a bug sweep
and who hears the characteristic "Donald Duck" over their TSCM equipment
knows that they are on to the trail of a live bug, and they will not sleep
for days until they find the thing.
Here is a photograph of the actual bugging devices, the physical dimensions
of this module is 35 x 23 x 8 mm (just under 1.5 cubic inches of volume)
for the first picture device and 31x19x6.1 mm for the other pictured
devices.




Here is a suitable transmitter circuit for the remote controller, based on
the RFM TX5000 module:
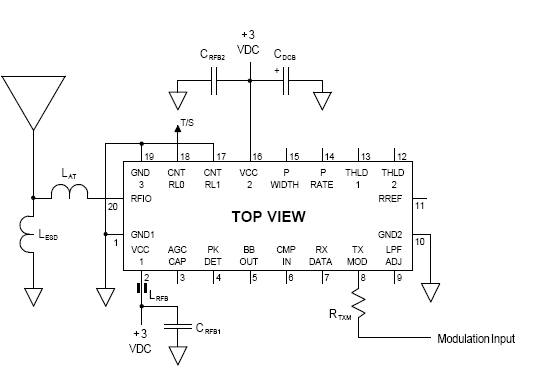
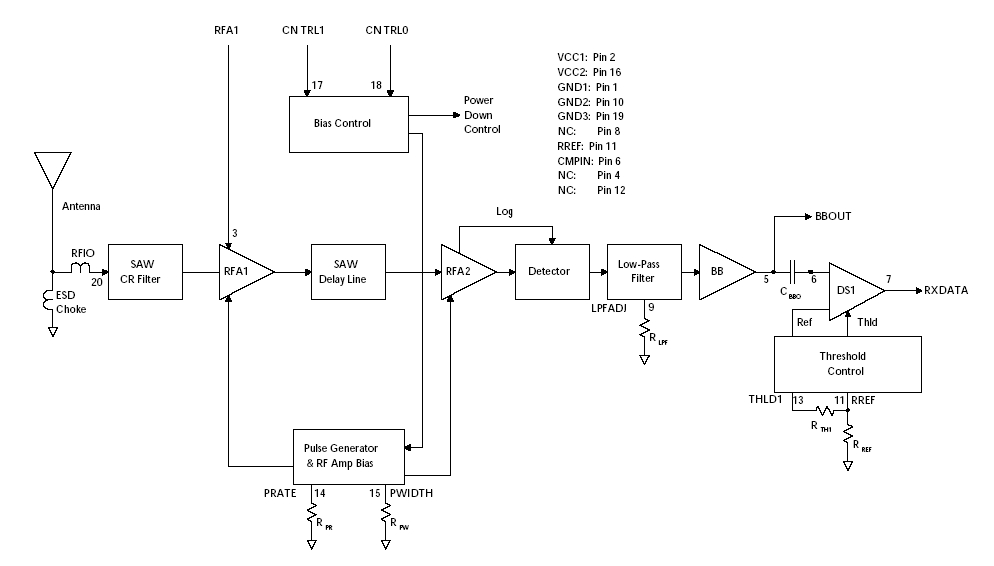
Here is a schematic for the receiver section of the bug, any engineering
student will notice a serious design anomaly that can be exploited by the
TSCM professional to hunt these devices down:
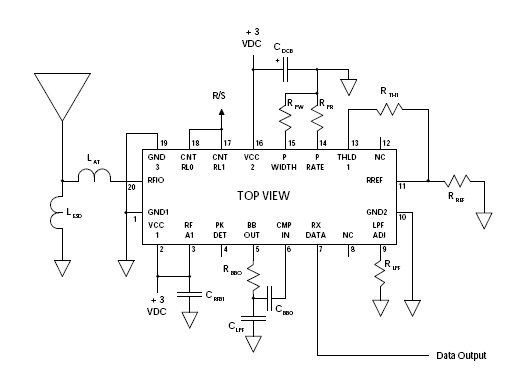
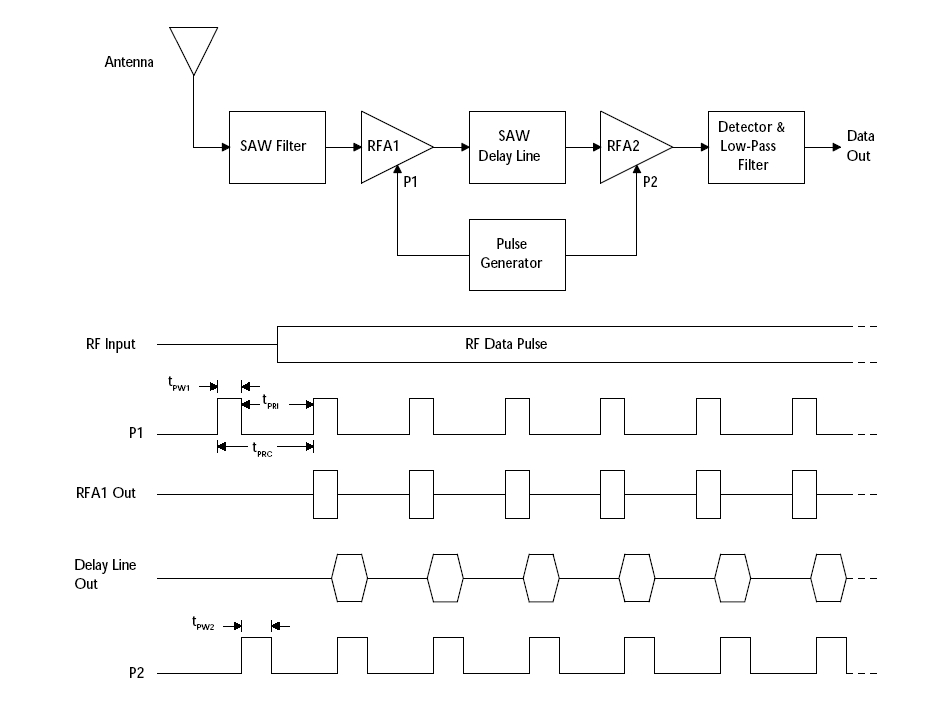
Here is a distributor listing for $3.00 modules that can be purchased and
programmed to wake these devices up and then put them back to sleep:
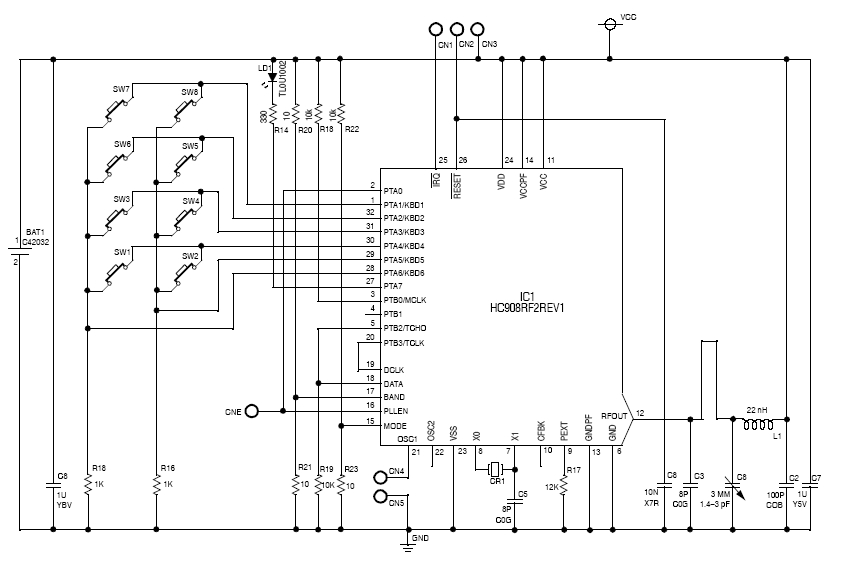
Here is a schematic for a garage door opener/prototype that can be used to
coax one of these eavesdropping modules to wake up and give itself up:
----------------------------------------------------------------------------------------------------
We Expertly Hunt Real Spies, Real Eavesdroppers, and Real Wiretappers.
----------------------------------------------------------------------------------------------------
James M. Atkinson Phone:
(978) 546-3803
Granite Island Group Fax: (978) 546-9467
127 Eastern Avenue #291 Web:
http://www.tscm.com/
Gloucester, MA 01931-8008 Email: mailto:jmatk[at]tscm.com
----------------------------------------------------------------------------------------------------
World Class, Professional, Ethical, and Competent Bug Sweeps, and
Wiretap Detection using Sophisticated Laboratory Grade Test Equipment.
----------------------------------------------------------------------------------------------------









